Immunity Passports - 5G - Vaccines. Total Control of You - Digitally. Sovereign Wealth Theft.
- Bruce Lamb

- Aug 3, 2020
- 18 min read
Updated: Aug 25, 2020

You are born through an act of God - A Natural Law through your parents. You are Given Dominion, Your Share, Over Land Air & Water. NATURAL - LAW. (ENGLISH)
At some point in History around the time of the Magna Carta 1215 dates the Catholic Church determined they represented God on the Planet and through the TRUST mechanism and Papal Bulls or Declarations they decided that they were to be the Administrators of the planet appointed by GOD? Ken Cousens And Santos Bonacci explain in their videos these historical aspects and what the Catholic Church or Vatican think they own extremely well. This is all about jurisdiction.
God - Man - Government - Fiction. Governments were created to serve the people - Men and Women, they are public servants and have oaths of office. There has to be transparency in their actions and have to work in our best interest otherwise in breech of oath - TREASON.
You are Sovereign beings free Men and Women till the Vatican/ Corporate machine that now controls Government (The Deep State or Hidden Hand) have gone rogue and into total ownership mode. Again.
This is today marketed as Agenda 21-2030 through the United Nations - New World Order initiatives become plain to see for those who have researched this subject matter.

Original RFID Technology:
Carl Sanders The Man Who Lead The RFID Development Team Speaks Out.. Designed to Tag Every Man Woman & Child. 666 is Built into an 18 Bit Computer. Three 6 Bit Bytes 6 - 6 - 6. Watch the Video Later in the Post.
20,000 took the chip in the hand when given the option of the card or chip.



Watch The Trans Human Agenda Video - Luciferase 060606 will Change Your DNA

The route cause of the problem is the Unlawful Conversion and Trespass exercised through the Birth Certificate system that without full disclosure of the terms to my parents took in my case and my parents case, Bruce-Robert to being Registered in the Vatican/ Jurisdiction world of DOG LATIN, BABYLONIAN BABBLE, ROMAN LAW to being BRUCE ROBERT LAMB using counterfeit means to fool all parties in the TRUST that was created without our knowledge. This is Theft of Sovereignty and Fraud.
Personally i have taken steps to correct this and wind back the clock. This is an ongoing process which we are to share with others as it impacts every aspect of our lives and futures. More so today than any other time in recorded history.


YOU - CANNOT - SEE - THE - LIE - TILL - YOU - KNOW - THE - TRUTH
(Romley-Stewart) This text is written in ENGLISH. Note The Hyphens?
As we will witness later in the collated information the Corona Virus is a LIE to The People created through an Act of Parliament - The Corona Virus Act 2020 and Bill. Confirmed here on the Govt website also is NOT a Highly infectious or Contagious disease: https://www.gov.uk/guidance/high-consequence-infectious-diseases-hcid

1. BE IT ENACTED - This is DOG LATIN and counterfeit. Babylonian Babble. Admiralty Law.
2. by the Queens most Excellent Majesty - The Queen is the Queen of Swans & Dolphins NOT England or anywhere in the UK shes a fraudster appointed by the Banksters a 3/16 Rothschild appointed 2.6.1953 by a rigged, bought infrastructure that effectively was a power grab by the Deep State/ Hidden Hand/ 13 Families or illuminati.
Call them what you want but they are fake and we have been defrauded. 2.6.1953 was the commencement of Silent Weapons Quiet Wars.
Affidavit and statements of Truth - Process Commenced 23.10.19
The Fraudulent Deep State Are Yet Again Looking To Take Away Your Sovereignty. Proven Through The Analysis Seen in the Connect The Dots Video plus Common Market/Brexit/ FCO 30/1048. What we already know is recorded across the following sites brought together in this post.
Its Now Crystal Clear That The Objective Is To Reduce The Numbers With A 5G/ Vaxx Combo As Witnessed in Wuhan. Results by 2025 recorded for the UK
on Deagel.com and then
Control The Masses or Reduced Numbers
Through "Tacit" Loss of Sovereignty
Taking Your Freedom & Committing
Human Rights Violations.
Stripped of Your Sovereignty, You Aren't Aware of Your Cestui Que Vie Trusts 1666 - Equity Trust or
Sovereign Wealth Fund Value?
This Is The Jackpot That Will Give The Bankster's A Global Payday Like No Other. On Your Death!!
Hence The Corona Virus Act and Bill.


See Downloads on linked Content.

Electro Magnetic Waves and Frequency Variations & Phase Shifts (Pulsed Signals) can be used to alter our DNA, Our Thoughts and when the Output Power is great enough turn us to dust. The original Microwave rooms that the Russians created, copied by the Americans from Cold War findings were used to do just this. Hence Paradise California and the Grenfell Tower incidents falsely covered in the media by mainstream reporters. Much of the evidence recorded by Mark Steele has been taken down by the You Tube Police under Govt (Hidden Hand) Authority?



We can now see their thought process in full, playing out in real time.
Often Referred To As The Totalitarian Tip Toe By David Icke, This Is Born Out Fully with Our Experiences To Date & This New Evidence That Underlines The Facts and IMPACT without redress Becomes Out & Out identity theft when Murder or Democide is NOT the result. Now using The Term Sovereign or SOVERIN to deceive the masses that remain.
The Babylonian Double Speak comes naturally as for centuries we have been exposed to DOG LATIN a Babylonian/ Admiralty/ Roman Law that is both Counterfeit and Deceptive to the masses, implemented through Acts and Statutes in Admiralty Courts.
I Know The V Code Product also Know Its Creator.
I DO NOT Think this is what he had intended for it? Or You & I
There is an External Force Guiding The Blueprint!!
The V Code Product Can Do The Job of Tracking, Tracing, Asset Management and Ability To Control Every Asset on The Planet. Including YOU!!.
Unless You Know Who You Are!!
Then Know What To Do?

ROSA KOIRE videos linked to Andy Burnham, GMCA and Mike Kane NOTICEs.
There IS NO PANDEMIC. This Is FAKE NEWS.

IGNORANCE - COMPLIANCE - CONSENT. Will Leave You Under The CONTROL of PRIVATE CORPORATIONS & THE BANKS THAT CONTROL GOVERNMENT.

Access into the proposed identity theft framework will be through quite innocent looking (To the misinformed) "Health Passports or Track & Trace" applications but the objective of the layered approach to Sovereignty loss is tiered in a technical TRUST style architecture and hidden from plain site within a communication model the majority will NOT comprehend.
There is NO full disclosure of the final objective. Its Deception, ID Theft. Its Fraud..
The development of these products is based on a Government Lie to the people who think that they are working in their best interest. They (Govt) are NOT!!

I was sent this book or PDF early 2019 and was intrigued as we are in the midst of an attack on many fronts - Economic and Physical. We cant see the truth unless we have had the need to dig and research but the links with Property overvaluation, Gold/ Silver price manipulation, plunder of Your Assets and Control were recorded well historically and those responsible identified and named by Major General Count Cherep Spiridovich. This is happening till today and more so NOW!!
A few key pages have been extracted in the post but a read of the publication id recommend as we can see how those who manipulate the UK and other Governments are single minded in purpose and time has only made them more open to verbalise their true intentions. Welcome To The New World Order

Mind mapping the Securities Fraud based on the Dylan Harvey Group Mortgage Securities Scam was the starting point after personal identification of a £200 Million securities fraud. I had bought apartments as investments which were over valued £40,000 each. Dylan Harvey Group sold 5000 similar units in the early 2000's.
This was my starting point after off plan property purchases 2006/7. My final proof of MP and Government cover up was confirmed 16th October 2018 then 30.11.18 after a meeting with Mike Kane MP Sale East & Wythenshawe. Much of this work is recorded across the Tangent Property Services website.
Mike Kane was tasked by Heather Buchanan APPG Banking Exec Director with asking John Glen the Treasury Minister a question set put together by myself.
16.10.18 he agreed at the meeting in Portcullis House Westminster, 30.11.18 He called me anti semitic and a conspiracy theorist. The questions were never asked in the House of Commons. Reason? Its Televised and the truth would get out.
The data provided indicated that the UK economy was being taken down by parties linked to HMRC, The Treasury, protected by the FSA then FCA, Police and Judiciary.
March 2020 They (Deep State AKA Government) are in the final stages of that take down.

Cross Referencing Independent Research - The Bernician.
Parliament Appears To Have Deposed QEII of Sovereignty
When Parliament recognised itself as ‘sovereign’ in section 38 of the European Union (Withdrawal Agreement) Act 2020, it did so after Boris Johnson, Ian Duncan Smith and Michael Gove spoke gushingly, in the run up to the December 2019 election, about how parliamentary sovereignty is borrowed from the People, via a democratic mandate.
I wrote this blog post on that very subject at the time, but I didn’t mention this obvious anomaly, since the in-coming government had already publicly and repeatedly declared that such sovereignty was dependent upon the democratic consent of the People that Parliament should exercise it.
Nevertheless, from this observation a question naturally arose:
If Parliament has only previously acted with the sovereign authority of the monarch, was the real intention of section 38 to depose QEII?

CONSENT, THE PRIMARY VICTORY - Do NOT Consent!
A silent weapon system operates upon data obtained from a docile public by legal (but not always lawful) force. Much information is made available to silent weapon systems programmers through the Internal Revenue Service. (See Studies in the Structure of the American Economy for an I.R.S. source list.)
This information consists of the enforced delivery of well-organized data contained in federal and state tax forms, collected, assembled, and submitted by slave labor provided by taxpayers and employers.
Furthermore, the number of such forms submitted to the I.R.S. is a useful indicator of public consent, an important factor in strategic decision making. Other data sources are given in the Short List of Inputs.
Consent Coefficients - numerical feedback indicating victory status.
Psychological basis: When the government is able to collect tax and seize private property without just compensation, it is an indication that the public is ripe for surrender and is consenting to enslavement and legal encroachment. A good and easily quantified indicator of harvest time is the number of public citizens who pay income tax despite an obvious lack of reciprocal or honest service from the government.
Silent Weapons Quiet Wars
The public cannot comprehend this weapon, and therefore cannot believe that they are being attacked and subdued by a weapon.
The public might instinctively feel that something is wrong, but that is because of the technical nature of the silent weapon, they cannot express their feeling in a rational way, or handle the problem with intelligence. Therefore, they do not know how to cry for help, and do not know how to associate with others to defend themselves against it.
When a silent weapon is applied gradually, the public adjusts/adapts to its presence and learns to tolerate its encroachment on their lives until the pressure (psychological via economic) becomes too great and they crack up.
Therefore, the silent weapon is a type of biological warfare. It attacks the vitality, options, and mobility of the individuals of a society by knowing, understanding, manipulating, and attacking their sources of natural and social energy, and their physical, mental, and emotional strengths and weaknesses.
READ THE COMPLETE DOCUMENT
Repeat:
CONSENT, THE PRIMARY VICTORY - Do NOT Consent!


DNA - CHANGES TO THE HUMAN RACE FOREVER!!



The Trans-Human Agenda Explored: Carbon, Graphene, Energy, Metals, Insulation, Modifying the Human Quantum.
What's in the Vaccinations?
A Self Healing Control Mechanism..
Delivered By Micro Dot.. It's a DNA Changer!! Luciferase.
Luciferase 060606 - Will Make You A Synthetic - A Non Human.




DIVERSION, THE PRIMARY STRATEGY
Experience has prevent that the simplest method of securing a silent weapon and gaining control of the public is to keep the public undisciplined and ignorant of the basic system principles on the one hand, while keeping them confused, disorganized, a nd distracted with matters of no real importance on the other hand.
This is achieved by:
(1) disengaging their minds; sabotaging their mental activities; providing a low-quality program of public education in mathematics, logic, systems design and economics; and discouraging technical creativity.(2) engaging their emotions, increasing their self-indulgence and their indulgence in emotional and physical activities, by:
(a) unrelenting emotional affrontations and attacks (mental and emotional rape) by way of constant barrage of sex, violence, and wars in the media - especially the T.V. and the newspapers.
(b) giving them what they desire - in excess - "junk food for thought" - and depriving them of what they really need.
(3) rewriting history and law and subjecting the public to the deviant creation, thus being able to shift their thinking from personal needs to highly fabricated outside priorities.
These preclude their interest in and discovery of the silent weapons of social automation technology.
The general rule is that there is a profit in confusion; the more confusion, the more profit. Therefore, the best approach is to create problems and then offer solutions.
Problem Reaction Solution - Hegelian Dialect - The Perfect Solution To A False Narrative. The Govt endorsed equivalent of a Child's soother.
Immunity Passports: Health Passport.




THE SOLUTIONS ARE AT HAND - WE ARE WORKING ON THEM NOW!!
Secured Party Creditor on behalf of Your STRAWMAN/ True Sovereignty - Know Who You are And Where The Money Came From?
YOU!! Your Signature - You Are The Value.
Affidavits of Truth and The Global 1933 Bankruptcy work in your favour.
Education is Key to Handling The Situation That Will Develop.
Its a House Of Cards - "Identify the Fraud" - "Identify The Trespass"
Follow The Money.. (CREDIT)
STEP 1. Level The Playing Field.

An attempt at Creating A New Digital Trust Mechanism - To Further Hide Sovereignty and Access to Your True Wealth. Stolen through A Babylonian, Admiralty - Roman Law Counterfeit contract(s) Deception..
Holder AKA Administrator
Verifier AKA Debtor
Issuer AKA Creditor
You The Man or Woman are the Creditor NOT The Issuer (FICTION) Robbery, Theft, Deceipt & Fraud are the future intentions of the Rogue Banking & Corporate Fraternity. The Final Proof. Thanks to many contributors.

TRUST LAW - YOU ARE THE BENEFICIARY AND THE CREDITOR. THE VATICAN AND The BANKS ARE THE ADMINISTRATORS & DEBTORS.
Laws of The Sea - Admiralty Law/ Roman Law/ Babylonian Law Apply to FICTIONS.
NOT Men & Women
Step 2: Understand the territory.



ID 2020 - Digital Identity Passport - Identity Theft. Sovereignty Lost..
A Play On Money Creation - The Cestui Que Vie Trust 1666 Cover UP.
Debt Enforcement & Control of The Human Being. Man - Woman, Child. Digital Slavery.


Alliance partners share the belief that identity is a human right and that individuals must have “ownership” over their own identity
Note: Identity of FICTION and Christian name(s) are two different things completely. BRUCE ROBERT LAMB is a DEAD FICTION Created by Government to control and enable Man & Woman into commerce. Bruce-Robert are my Christian names : LAMB is a name provided by the Government and the Vatican as part of the Cestui Que Vie Trust 1666
Cestui que vie remaining beyond Sea for Seven Years together and no Proof of their Lives, Judge in Action to direct a Verdict as though Cestui que vie were dead.
If such person or persons for whose life or lives such Estates have beene or shall be granted as aforesaid shall remaine beyond the Seas or elsewhere absent themselves in this Realme by the space of seaven yeares together and noe sufficient and evident proofe be made of the lives of such person or persons respectively in any Action commenced for recovery of such Tenements by the Lessors or Reversioners in every such case the person or persons upon whose life or lives such Estate depended shall be accounted as naturally dead, And in every Action brought for the recovery of the said Tenements by the Lessors or Reversioners their Heires or Assignes, the Judges before whom such Action shall be brought shall direct the Jury to give their Verdict as if the person soe remaining beyond the Seas or otherwise absenting himselfe were dead.
Step 3: Remedy
Common Law Courts - Remedy Toward Who You Are.

Bruce-Robert: Lamb Recorded as a living Man
CLC plus Knowledge Based Strategies
Will Now Set You Free.

ID2020 - Applies To The FICTION/ PERSON NOT
The Man or Woman. https://id2020.org/manifesto
In 2018, ID2020 Alliance Partners, working in partnership with the United Nations High Commissioner for Refugees (UNHCR), drafted a formal articulation of our perspective on ethical approaches to digital identity. The landmark ID2020 Alliance Manifesto below lays out these shared principles and forms a starting point to guide the future of digital identity globally.
The Alliance Manifesto (The Deception Starts)
1. The ability to prove one’s identity is a fundamental and universal human right.
2. We live in a digital era. Individuals need a trusted, verifiable way to prove who they are, both in the physical world and online.
3. Over 1 billion people worldwide are unable to prove their identity through any recognized means. As such, they are without the protection of law, and are unable to access basic services, participate as a citizen or voter, or transact in the modern economy. Most of those affected are children and adolescents, and many are refugees, forcibly displaced, or stateless persons.
4. For some, including refugees, the stateless, and other marginalized groups, reliance on national identification systems isn’t possible. This may be due to exclusion, inaccessibility, or risk, or because the credentials they do hold are not broadly recognized. While we support efforts to expand access to national identity programs, we believe it is imperative to complement such efforts by providing an alternative to individuals lacking safe and reliable access to state-based systems. 5. We believe that individuals must have control over their own digital identities, including how personal data is collected, used, and shared. Everyone should be able to assert their identity across institutional and national borders, and across time. Privacy, portability, and persistence are necessary for digital identity to meaningfully empower and protect individuals.
6. Digital identity carries significant risk if not thoughtfully designed and carefully implemented. We do not underestimate the risks of data misuse and abuse, particularly when digital identity systems are designed as large, centralized databases.
7. Technical design can mitigate some of the risks of digital identity.
Emerging technology — for example, cryptographically secure, decentralized systems — could provide greater privacy protection for users, while also allowing for portability and verifiability. But widespread agreement on principles, technical design patterns, and interoperability standards is needed for decentralized digital identities to be trusted and recognized.
8. This “better” model of digital identity will not emerge spontaneously. In order for digital identities to be broadly trusted and recognized, we need sustained and transparent collaboration aligned around these shared principles, along with supporting regulatory and policy frameworks.
9. ID2020 Alliance partners jointly define functional requirements, influencing the course of technical innovation and providing a route to technical interoperability, and therefore trust and recognition.
10. The ID2020 Alliance recognizes that taking these ideas to scale requires a robust evidence base, which will inform advocacy and policy. As such, ID2020 Alliance-supported pilots are designed around a common monitoring and evaluation framework.
Note: There is NO Pandemic and the false Narrative Trigger Event 201 set the trajectory toward the planned New World Order Genocide in keeping with Planned Parenthood's founder indoctrinated son. Bill Gates
Gates: If Anything Kills Over 10 Million People Today - It Wont Be A Missile But A Virus.
Event 201: Predicted Exponential Rise In DEATHS

DEAGEL DEATH STATS FORECAST - GLOBAL http://www.deagel.com/country/forecast.aspx

Corporate Identity Theft - Leg-itimized? NOT Lawful.
Extract: Premise Based on A Lie.
The white paper is intended to further the public discourse about immunity certificates and ensure that such systems are developed consistent with the principles outlined in the ID2020 Manifesto for digital ID (developed in 2018 in partnership with the UN High Commissioner for Refugees).
The Technical Requirements that underlie the ID2020 Certification also provide a valuable road map to assist technology providers and governments in the development of ethical, inclusive digital identity solutions, including digital health credentials.
BORIS & THE SAGE SLIP UP - Scientific Advisory Group for Emergencies




Luciferase 060606
Address to the UN September 2019 Refers To 5G - Every Citizen Round The Clock Surveillance.
Then By March 2020 He Kicked It Off For The UK!!
We are a resource Click By Click/ Your Data is King.
Digital Dystopian Interference Is Upon Us.
BoJo Refers To The Anti Vaxxers?
Fears - Who Now Have Good Reason.
COVid - 19 Fixes, Quinine, Zinc, Hydroxychloroquine..
NOT Untested Killer Vaccines when linked with Microwave Technologies AKA 5G/ Radar/ Radio/
60 GHz/ WiGiG Tech.



Widespread social distancing orders have proven an effective strategy for containing the spread of the virus. But these strategies are not without significant economic, social, and psychological consequences. The time is now to begin planning for the next phase of the COVID-19 response and recovery. “If we need to do immunity certificates”, said Gruener, “let’s make sure we do them right.”



COVID CREDENTIALS?
So we have a false Pandemic and its an opportunity to Kill Millions, Wreck Businesses & Issue "Immunity Passports To The Masses. All Based on A Lie?
Boris Explain This One Away - If You Can. Id Say its TREASON or High Treason?

Immunity Passports USA

Restricted Travel, Access to Events, Track Trace & Business Rules Determine Who You Meet & Where You Go. Agenda 21/ 2030, New World Order, World Economic Foundation Narrative. Sovereignty Loss.

Features
Closed Loop Security. Only VSTE scanners can authenticate a VCode
Custom Content Delivery - Direct content delivered from one scan
VPlatform portal allows users to create, manage and analyse VCodes
Scan from up 100 metres and down to 225 Microns
Dynamic Content: Update content at anytime without changing the VCode
Full Scan Analytics - Track who, what, when and where
Permission Based Content Access - Who, What, Where and When
Full Swagger API Toolset available for system integrations
Collision Free System - VCode duplication can never happen
Virtually Unlimited Supply of VCode futureproofs your solution
Benefits
End-to-end tracability and content delivery throughout the supply chain
Real Time Tracking; Track, trace and verify authenticity of goods.
Bespoke end user content delivery - Links, documents, videos, content
ID, qualification, certification, training and membership verification
VCodes Successfully tested & scanned down to 225 Microns
Accept Instant, secure and transparent Digital & charity payments.
Full API stack for system integration
Analyse user behaviour patterns, traffic and workflows
Scan user data capture metrics for compliance and evidentiary outputs
Video and FMCG traceablility, preventing counterfeit and piracy



Self Sovereign Identity Groups?
Businesses that will Administer your Electronic/ Digital You?
A Play On Your True Standing To Fool The Masses and The Mis Informed By The Hidden Hand - The False Govt.

ONE WORLD GOVERNMENT - NEW WORLD ORDER

WHO OWNS WHICH BUSINESS?



The Issue For Them (Deep State) Is Getting YOU Registered On These Systems?
Whose The Guardian? Whose The PERSON?
Whose The Dependent?

The Layered Approach To Digital Slavery

I4A Identity 4 All?

The Sovrin Solution
It’s time to evolve the current system of siloed identities, endless passwords, and insecure databases.
The time is here for the frictionless, secure identity verification of self-sovereign identity.
The Sovrin Network is the new standard for digital identity – designed to bring the trust, personal control, and ease-of-use of analog IDs – like driver’s licenses and ID cards – to the Internet.
We’ve designed Sovrin as a metasystem for any application to use, giving people, organizations, and things the freedom to prove things about themselves using trustworthy, verifiable digital credentials.
“Self-sovereign” means the individual identity holder controls their credentials, using them whenever and however they please, without being forced to request permission of an intermediary.


Theft of Sovereignty - You Become An Owned Piece of Digital Property - Slavery - Treason.

God - Man - Govt - Fiction


V CODE AT THE CORE?

The Four Layer Digital Slavery Stack

HANSARD 1803–2005 → 1810s → 1815 → June 1815 → 13 June 1815 → Commons Sitting BILL TO PREVENT ILLICIT IMPORTATION OF SLAVES.
HC Deb 13 June 1815 vol 31 cc772-85 Mr. Wilberforce rose, pursuant to notice, to bring under the consideration of the House, his motion respecting the registry of slaves in the British colonies.
He felt a satisfaction, he said, in thinking that the measure which he intended to propose was one which involved no novelty of principle, but was, in fact, merely a supplement to the Bill for the abolition of the Slave-trade. It had been already adopted, to a certain extent, in the island of Trinidad, after a most mature and deliberate investigation, and had proved highly beneficial. He was happy to add also, that the principle of the measure was one which had received the decided approbation of the late Mr. Perceval, and which it had always been his intention to extend to those colonies which have colonial legislatures, as well as to those which had not.
He was concerned to hear, however, that he might expect to receive opposition from many gentlemen in that House, who represented the West-India interest in it; and that opposition rendered it the more necessary that he should distinctly state the great principle upon which he intended to rest his measure. The object of it was not merely to check the various means by which the abolition laws were evaded or violated, but to prevent the continuance of the source of the evil itself
ID 2020 Proves That Slavery was NEVER Abolished. They Just Changed The Terms of Reference. The 1933 Global Bankruptcy and Birth Certificate System made man and woman the true value in the system. The Bankruptcy though was completed through various acts of FRAUD through counterfeit DOG LATIN contracts and ACTS & Statutes.
We, You And I Are The Creditors in The Trust and Once Again They are attempting to make us The Debtor. This though is The Banker/ Administrators Role. Deception & Theft.

Equity & Trusts 4Th Edition - Alastair Hudson



REPEATED - FOR LEVEL OF IMPORTANCE
Patent 060606
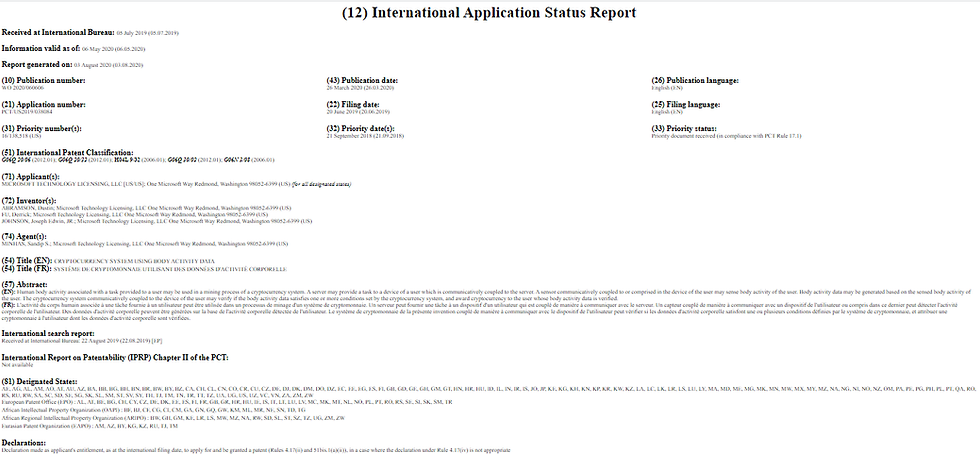
(54) Title (EN): CRYPTOCURRENCY SYSTEM USING BODY ACTIVITY DATA(54) Title (FR): SYSTÈME DE CRYPTOMONNAIE UTILISANT DES DONNÉES D'ACTIVITÉ CORPORELLE
(57) Abstract:(EN): Human body activity associated with a task provided to a user may be used in a mining process of a cryptocurrency system. A server may provide a task to a device of a user which is communicatively coupled to the server. A sensor communicatively coupled to or comprised in the device of the user may sense body activity of the user. Body activity data may be generated based on the sensed body activity of the user. The cryptocurrency system communicatively coupled to the device of the user may verify if the body activity data satisfies one or more conditions set by the cryptocurrency system, and award cryptocurrency to the user whose body activity data is verified.

A Microchip For ID To Catch Drug Shipments -
Govt Story line? This was a Lie.
1/4 of a Grain of Rice in Size - Lithium Battery
Chip Location: The Temperature Change is Most Rapid on Forehead and Between Thumb & Forefinger: Book of Revelation 13: 16-17 . References.
18 Bytes ID Address 6+6+6

The Cashless Society. The New World Order, One World Government, The Fulfillment of Prophecy. No Man Might Sell UNLESS HE HAS THE MARK (President CLINTON)
When Did This Start: A Christian cannot belong to a Secret Society.

From The Book of Genesis To Revelation - Identifies Some of The Answers:




Revelation 16:2



You Cannot Buy Sell or Trade Without This Mark?
Chipped USA.





The Wuhan Experience - A Travelers Record - White - Red - Yellow - Green?
Who or What Are You?

Street Spot Checks

Life in the Digital Gulag: https://www.5gmediawatch.com/post/orwellian-future-from-covid-19-to-remaking-us-uk-western-society
China’s Vanishing Muslims: Undercover In The Most Dystopian Place In The World




To Get You Into The System..
V Code at the Core. Health Passports at the Periphary.
Whose involved?





100 Plus Brands. Associated with evernym?


TRUST ECO SYSTEM.

Corporate Enslavement. Planned 1945
The Red House Report


YOU CAN BE DIGITALLY OWNED - OR FREE
- ITS YOUR CHOICE

YOU BECOME THE DEPENDENT - THE CHILD

Identifiers and Discovery
A key piece of the decentralized identity equation is how people, organizations, and devices can be identified and located without centralized systems of identifiers (e.g. email addresses). DIF members are actively working on protocols and implementations that enable creation, resolution, and discovery of decentralized identifiers and names across decentralized systems, like blockchains and distributed ledgers.
Claims and Credentials
The ability to verify the claims and assertions of identities is key in establishing trust among entities on a decentralized system that lacks a centralized hierarchy. DIF has recently begun work on defining the specs, protocols, and tools it can provide to the ecosystem to help ecosystem participants and their customers easily integrate DID-signed claims into their apps and services.
Sidetree Development & Operating Group
The development and maintenance of the formal Sidetree specification, and a hub of coordination for Sidetree-based DID Method node operators. This group also generates libraries, tooling, and documentation to aid Sidetree-based DID Method node operators.
DID Communication
Produce one or more high-quality specs that embody a method (“DIDComm”) for secure, private and (where applicable) authenticated message-based communication, where trust is rooted in DIDs and depends on the messages themselves, not on the external properties of the transport(s) used.
Anything Ever Made - Anything Ever Grown - You Cant Have Access to without A COVid-19
Certificate of Vaccination Identification ID 19.
The Pandemic That NEVER Existed
The Agenda 21/ 2030 Trigger






Comments